TL; DR: As reported by Wired, nearly 100 million cars manufactured and owned by the Volkswagen group for the last 20 years can be opened wirelessly as a result of a hack. Just listen to the radio transmission when you open the car, process it… and voila. This was presented in detail at Usenix Conference in 2016. According to the researchers, the following models are susceptible (for the models in bold researchers showed Proof of Concept, others indicated as probably susceptible):
Audi: A1, Q3, R8, S3, TT, various other types of Audi cars (e.g. remote control part number 4D0 837 231)
VW: Amarok, (New) Beetle, Bora, Caddy, Crafter, e-Up, Eos, Fox, Golf 4, Golf 5, Golf 6, Golf Plus, Jetta, Lupo, Passat, Polo, T4, T5, Scirocco, Sharan, Tiguan, Touran, Up
Seat: Alhambra, Altea, Arosa, Cordoba, Ibiza, Leon, MII, Toledo
Škoda: City Go, Roomster, Fabia 1, Fabia 2, Octavia, SuperB, Yeti
The wireless key mechanism is based here on only a few major cryptographic keys (master keys) – the same for many different car models. The keys can be pulled out and combined with additional information eavesdropped during the opening of the car.
In result of the combination of these two pieces of information, the machine may be unlocked.
Other producers are also vulnerable, though in a slightly different way – details later in the text.
The cost of this fun? About $40 (+ battery cost) for equipment in a ‘grazed’ (automated) version. In reality it’s just an appropriate Arduino:

Before we go any further – a bit of history. Modern car keys – in wireless versions – consist of two components: The first one lets you open the car door; the second allows you to start the engine. These components can be closely related, although they do not have to be:

Sometimes, it’s possible to break both components right away, sometimes only one. Historically, this is how it was: In 2005, it was shown how to break the DST40 algorithm used in immobilizers (it had barely a 40-bit encryption key), and in 2012 hitag2 . Here the result was:
The authors showed that an attacker can obtain the 48-bit secret key required to bypass the electronic protection in less than 360 seconds.
At the Usenix party last year, wireless lockpicking was also shown. This time, Megamos Crypto has fallen, used in such brands as Audi/Fiat/Honda/Volkswagen or Volvo. Here, due to various weaknesses, we managed to recover the 96-bit crypt key in the car key:
In this paper we have reverse-engineered all proprietary security mechanisms of the transponder, including the cipher and the authentication protocol, which we publish here in full detail. This article reveals several weaknesses in the design of the cipher, the authentication protocol, and also in their implementation. We exploit these weaknesses in three practical attacks that recover the 96-bit transponder secret key.
When it comes to the history of RKE (Remote Keyless Entry) mechanisms – historically, first systems appeared without any cryptography (for example, researchers mentioned about Mercedes like this from 2000); later it was so-called rolling code.
In short, it consists of downloading certain values from the key, adding the counter value to it and sending the whole in an encrypted form to the car. The car remembers the last correct value of the counter, which effectively protects against a replay attack (i.e. I cannot overhear the radio communication and later successfully use it to unlock the car).
Of course, if I retrieve the cryptographic key from the car key or the encryption algorithm itself only averagely safe, the protection is compromised. For example, this type of attack is described in a presentation with a rather emphatic title: “How To Steal Cars -A Practical Attack on KeeLoq” or in 2014 here:
An adversary has to eavesdrop three subsequent rolling codes. Then, using phase-space analysis, the next rolling code can be predicted with a high probability.
How did the researchers get to work? They picked up the selected key models first and ejected them from the electronics. For example, such a toy:
includes a 4-bit MARC4 processor. The source code of the program executed on this processor can be extracted from the ROM by… microscopic analysis (bit by bit). Researchers went a little differently and pulled out (in a simple way) the firmware on the other side of the communication (i.e. from the car) – from the so-called ECU. In this way, they detected several communication patterns used in Volkswagen group cars (referred to below as VW-1 to VW-4). The first from the line:
In conclusion, the security of the VW-1 is solely based on obscurity. Neither is there a cryptographic key involved in the computation of the rolling code, nor are there any vehicle or remote control specific elements for some form of key diversification.
I guess it is even more interesting in the VW-2 and VW-3 types:
Both schemes use a fixed, global master key independent of vehicle or remote control. In other words, this means that the same AUT64 key is stored in millions of ECUs and RKE remotes, without any key diversification being em- ployed at all.
It can be said that these previous patterns are a bit older, but also in VW-4 (e.g. shown here, Audi Q3 from 2016) is susceptible:
However, again we found that a single, worldwide key is used for all vehicles employing the VW-4 system. The same single point of failure of the older systems VW-1–VW-3 is hence also present in recently manufactured vehicles. For example, we found this scheme implemented in an Audi Q3, model year 2016, and could decrypt and generate new valid rolling codes to open and close this vehicle.
Attentive readers of the original study know that this is not all. Researchers examined another encryption scheme used in the keys of other manufacturers: hitag2. Here, they managed to prepare a practical attack – however, it requires listening to 4-8 opening of the car (+ 1 minute work from a laptop). Earlier there were successful hacks, but they required much larger eavesdropping samples.
On average, our attack implementation recovers the cryptographic key in approximately 1 minute of computation, requiring a few eavesdropped rolling codes (between 4 and 8).
Examples of vulnerable models? Here we go:
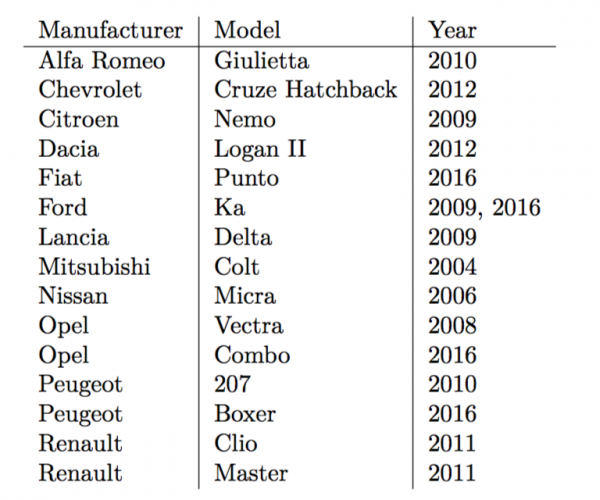
And to be sure, confirmation of the effectiveness:
We verified our findings in practice by building a key emulator and then unlocking and locking the vehicles with newly generated rolling codes. (…) The vehicles in the above list are our own and also those of colleagues and friends who volunteered.
The authors showed the effectiveness of the attack from a distance of approx. 90 meters, but they indicate the possibility of potential eavesdropping of keys from a distance of up to 1 km (work: Eavesdropping and detection of active RFIDs and remote controls in the wild), which in combination with the possibility of DoSing a car (often, to deactivate the car owner’s key, it is enough to send an “incorrect” package several times), rather unpleasant possibilities.
Finally, it is worth mentioning that according to the researchers, VW confirmed the vulnerability, but on the basis of a separate agreement, the researchers agreed, among others, to not publish the extracted universal cryptographic keys:
VW Group acknowledged the vulnerabilities. As mentioned in the paper, we agreed to leave out, amongst others, the following details: cryptographic keys, part numbers of vulnerable ECUs, and the used programming devices and details about the reverse-engineering process.
We remind you that all information is published here for educational purposes only. We do not recommend using it unlawfully.