Introduction
In recent years phishing has evolved very much. The emergence of many new techniques – and therefore the modification of available solutions – has taken this type of attack to a higher level. Attackers increasingly use e-mail, websites or private messages in instant messengers to distribute it. In this article I will try to introduce one of the most popular methods currently used in phishing campaigns.
The aim of this article is to raise public awareness that phishing is no longer just about sending a message with a fake website and trying to extort our password to the mail – sometimes it is a much more advanced and better strategically planned attack. It is worth to learn about these “atypical” methods, because perhaps their knowledge will protect us from the danger.
Typosquatting
Typosquatting consists in registering domains with the use of simple typing errors, which can be made by Internet users when entering the name of the page in the address bar of the browser. An example could be omitting one of the letters or entering one that is adjacent to a letter on the keyboard.
Other simple applications of this technique are:
- wwwdomainname (without a dot between “www” and the domain name)
- www-domainname (the line between “www” and the domain name)
- domainname-anyname (the line between the original domain name and the domain name)
It is worth mentioning that in the past the most popular was to place a directory with the domain name under which the attacker wanted to impersonate on the “taken over” by the attacker.
An interesting analysis of typosquatting, based on an overview of over 500 popular websites, can be found at the following address:
Homoglyph & homograph
An attack involves using similarities in the appearance of a given letter, number or character by using a set of other characters, including numbers and letters. A common method is to use the same letters from other languages or coding.
The simplest technique of this type is to combine letters and characters and replace them with other ones. The most popular examples include the following (the more readable version is presented in brackets):
- rn as m (lower case letters R and N as lower case letter M)
- cl as d (lower case letters C and L as lower case letter D)
- q as g (lowercase letter Q as lowercase letter G)
- cj as g (lower case letters C and J as lower case letter G)
- vv as w (double letter V as letter W)
- ci as a (lower case letters C and I as lower case letter A)
- I as l (capital letter i as lowercase letter L)
- l as I (lower-case letter L as upper-case letter i)
- 1 as l (digit 1 as lowercase letter L)
- 1 as I (digit 1 as capital letter i)
- l as 1 (lowercase letter L as a number 1)
- I as 1 (capital letter i as number 1)
In the case of a different language and encoding, you will find a large list of character equivalents on the following page:
- https://github.com/codebox/homoglyph
- http://homoglyphs.net/?text=tutajnazwa&update=update&unicodepos=1&print=1&lang=en&exc2=1&exc3=1&exc7=1&exc8=1&exc13=1&exc14=1
- http://www.fileformat.info/info/unicode/block/index.htm
The Windows “Windows Character Map” tool should also be used (charmap.exe).
Additional links:
Punycode
Punycode is a special encoding that is used to convert Unicode into a set of allowed characters in the name (i.e. ASCII letters, digits and hyphens). A domain that contains characters from outside ASCII is called Internationalized Domain Name (IDM) – thanks to Punycode we are able to present its name in the version supported by DNS servers:
| Unicode | Punycode |
| seĸuraĸ.pl | xn--seura-v5ad.pl |
IDN Conversion Tool: http://mct.verisign-grs.com/
Bitsquatting
Bitsquatting is a technique of registering a domain that differs by one bit from the “popular” one, under which the attacker would like to impersonate himself. The whole is based on the expectation of random errors caused by computer hardware (usually RAM).
An interesting study of this issue was presented under the link: http://dinaburg.org/bitsquatting.html.
However, a domain using the above method can be generated, e.g. using scripts: https://github.com/benjaminpetrin/bitsquatting or https://github.com/artemdinaburg/bitsquat-script.
Right-to-Left Override [RTLO / RLO]
Over the last few years we have been able to see different methods of using the “Right-to-Left Override” mark. (Code: U+202E):
- from changing the file extension:
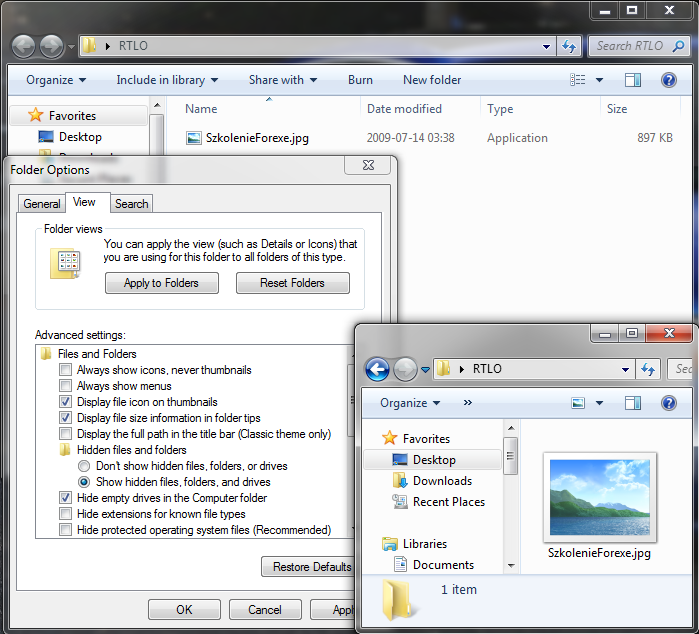
Note: As file extensions, e.g. EXE and SCR, when using the RTLO mark are displayed vice versa, i.e. EXE and RCS (in a traditional technique without obscuring the original extension with different methods), criminals often use words that have the above ends (or similar), e.g. EXE and SCR: Annexe, Forexe, Reflexe, Arcs, Orcs, Marcs.
Today I will present a less popular method that attackers may use to “spoof” email links.
I wrote “may” because I’m not sure if they really use it. I came across this possibility of using the RTLO mark myself – however, it is quite easy to use, so probably someone else has already discovered it as well.
Attackers place an HTML code on a website containing a “mailto:” link with a RTLO sign (URL Encode – %E2%80%AE):
|
1 2 |
<a href="mailto:%E2%80%AEot.lawzor@sekurak.pl">lp.karukes@rozwal.to</a> |
The purpose of the above example was to present the e-mail “lp.karukes@rozwal.to” in a mail program, e.g. Microsoft Outlook, but eventually send it to the address “ot.lawzor@sekurak.pl”.
When the attacker clicks on the above link in the email program we will see:
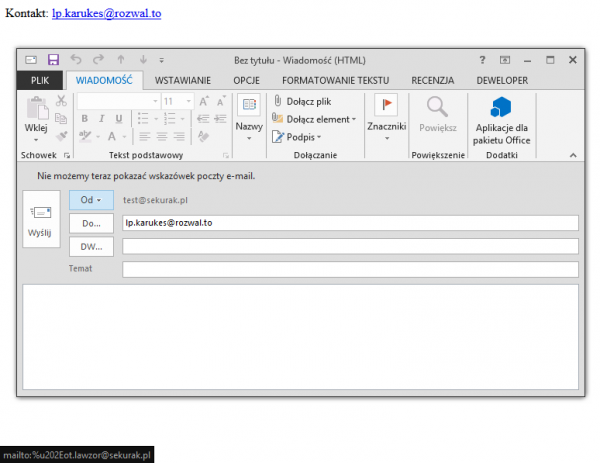
Picture nr 2. Microsoft Outlook 2013 New Message Creation window with a false address in the “To” field
However, after clicking the “Send” button, the e-mail will be sent to another address. If the victim moves the mouse to the address field, they will also see a “fake” e-mail:
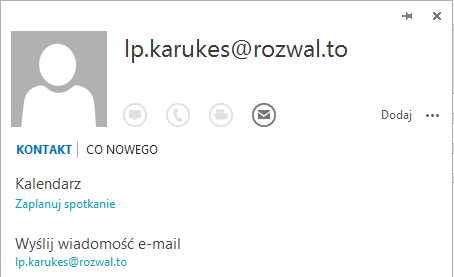
Let’s always carefully check the recipient of our e-mail. If possible, let’s try to manually rewrite the e-mail address to which we want to send the message and don’t click on unknown links.
URI scheme
Uniform Resource Identifier (URI) is a string of characters used to identify resources. Thanks to it, we can, among other things, place an image on a page (in HTML code) without the need to attach additional graphic files. This makes it much easier for criminals to do a lot of things, while at the same time reducing the detection rate (less traffic is generated, boils down to downloading 1 HTML page) and makes sure that nothing is loaded from the outside.
The most popular schemes used by “phishers” include:
- data:MIME,VALUE
- data:MIME;charset=CODING;base64,VALUE_IN_BASE64
- data:,VALUE
The VALUE field depends on the type of file or the encoding used.
HTML5 Fullscreen API Attack
The “HTML5 Fullscreen API” attack uses a full-screen mechanism to present web content. Feross Aboukhadijeh (http://feross.org) is the author of the “unusual” presentation of the implementation of the API. Criminals, using the mechanism, are able to present a false view of the top bar of the browser and load any lower content, so that a reckless user may not notice “substitution”.
Blankshield & Reverse Tabnabbing
The attack consists in swapping the content of the bookmark from which you clicked (target=”_blank”) on another page.
How the attack works in practice, we can check by opening a page in the browser (preferably Google Chrome): https://sekurak.pl/przyklady/blankshield_reverse_tabnabbing/, then check the previous card.
On the page: : https://samiux.blogspot.com/2016/09/firefox-480-does-not-vulnerable-to.html presents an interesting summary of what browsers are susceptible to this attack.
It is worth mentioning that Google decided not to pay out prizes (Bug Bounty) for errors of this type: https://sites.google.com/site/bughunteruniversity/nonvuln/phishing-with-window-opener.
Clickjacking
The attack consists in creating an element (usually an iframe), which will be displayed above other functionality of the service. The implementation of this attack we could observe many times some time ago, when many pages were created, which covered the “Like it!” button from Facebook (now the popularity of this attack has decreased). An unaware user who clicked on a link actually agreed to like that fan page.
Redirect URL
The technique consists in using trust to another website and finding an error or functionality on it that will allow to enter the address to which the redirection will take place (OWASP TOP 10 from 2013, point A10). Therefore, the attack scheme could look like this:
- the attacker finds a redirection functionality on a trusted website that does not verify the destination address.
- The attacker creates a fake phishing site on its server.
- the attacker sends a “sociotechnical” email to the victim of the attack with a link:
|
1 |
https://trustedpage/index.html?redirecting=http://attackerspage/phishing.html |
The victim of the attack, hovering the mouse over the hyperlink, sees the address “https://trustedpage/” at the beginning, which may confirm their belief that the website is safe.
Content Warning Bypass
Probably the reader has already seen a message that only HTTPS content has been displayed. This happens mainly when you are on a website with HTTPS, but e.g. in the iframe there is a page that does not have an encrypted connection (HTTP). Below is an example:
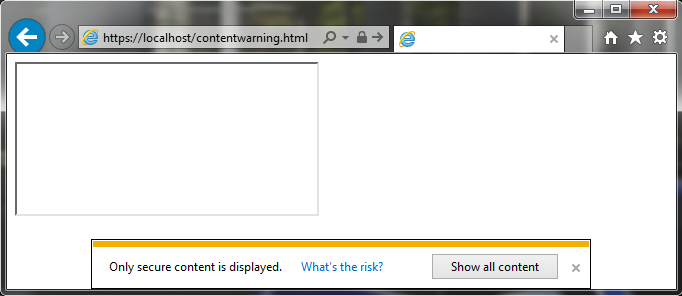
Some time ago, however, an article appeared on the BrokenBrowser.com website, where the author informs about an interesting trick. In order to load a HTTPS page, e.g. an iframe with HTTP source, it is enough that we use another HTTPS page, which has the functionality of redirecting the user to any website.
A sample code could look like this:
|
1 |
<iframe src="https://pagezhttps/index.php?redirecting=http://maliciouspageadress"></iframe> |
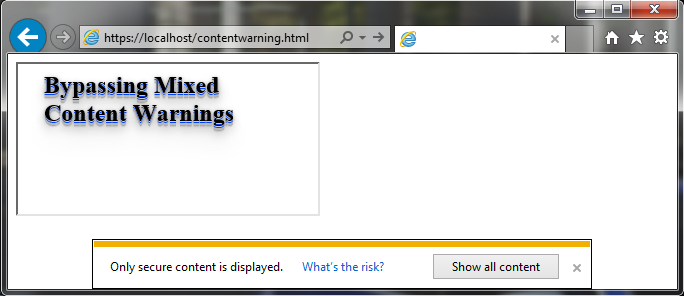
Thanks to this technique, criminals can easily bypass this restriction.
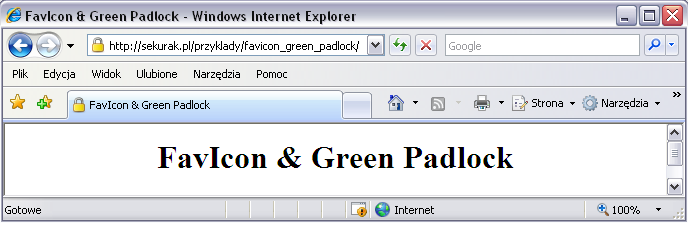
Favicon & Green Padlock
This is a simple technique, which is now hardly used anymore due to changes in the presentation of the place where the page icons are displayed. Attackers created a favicon with a green or yellow padlock that suggested that the site had a secure HTTPS connection.
HTTP Auth
Some time ago we described the Phishery tool, which allows you to add a “reference” to a template on a “remote server” to an existing Word document, in a window similar to the one below:
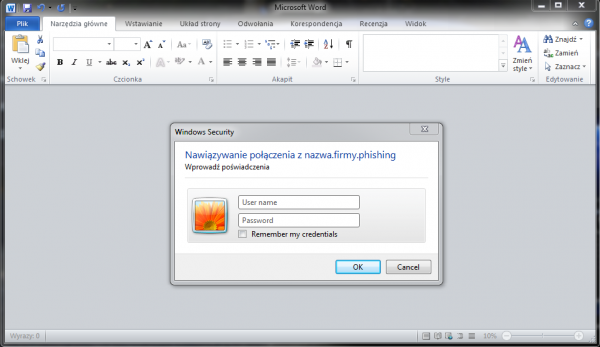
If the attack victim provides login details, e.g. to their domain account, the attacker will automatically receive them:
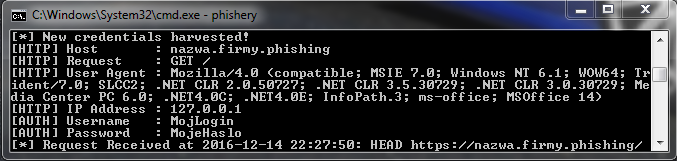
It is worth knowing that this type of attack can also be used in e-mails – in Microsoft Outlook after sending a message with a link that is protected by HTTP Basic Authentication. A victim of an attack who receives an e-mail prepared in this way will see a screen similar to the one below (depending on configuration):
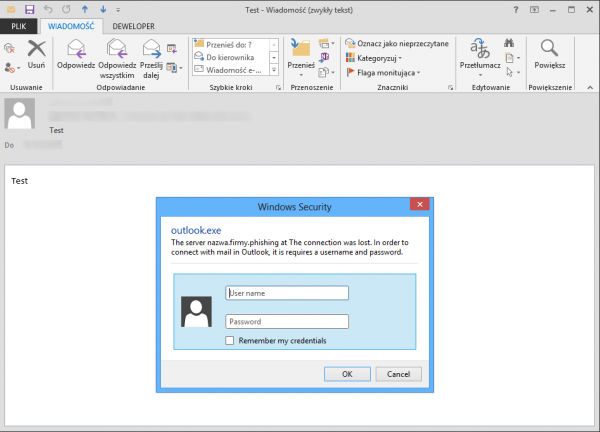
The attacker hopes that the victim of the attack will enter their login data in such a pop-up window.
By default, the message has a circuit diagram: ”The server ATTACKER_SERVER_NAME at VALUE_AUTHNAME_FROM_FILE_.HTACCESS requires a username and password”. In the AuthName value field from the .htaccess file, the attacker most often writes his request. In the above example the request, i.e. “The connection was lost. In order to connect with mail in Outlook, it is…”, was written in such a way that it “connects” to the default text, i.e. “requires a username and password”.
Remember to NEVER enter passwords in such pop-up windows whose domains we do not know! Let’s watch out for this type of attack, as it’s becoming more and more popular!
“Name” field with e-mail address and spaces
A few years ago (about 2011), while performing social engineering tests for one of the clients, I came up with an idea of using “hiding an e-mail address” if the “Name” field is too long.
I have not seen the use of this technique in practice, nor have I read about it, but it is worth considering this possibility. In order to execute this attack, the offender enters the schematic value in the “Name” field:
So after sending a message with the above field (but without 300 spaces), the recipient will see:
|
1 |
Name and surname <False@adress.email> [300 SPACES] |
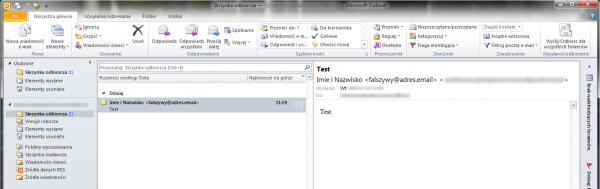
Of course, the real address has been blurred only for the purpose of the drawing for this article.
But what happens when you add the 300 spaces? The view will be as follows:
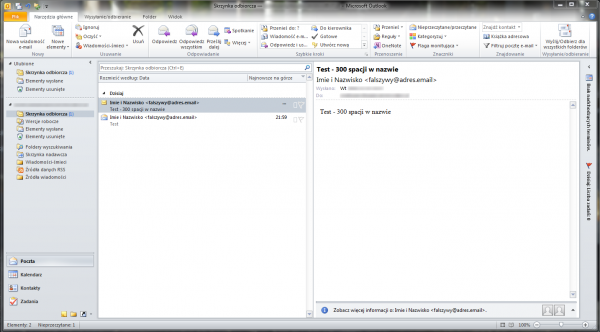
This is because, depending on the resolution, characters that do not fit on the screen are hidden by Microsoft Outlook – so our “long value” of the “Name” field is not visible (in most cases 300-500 spaces are enough).
And that’s what the view looks like when you click on the “Answer” button:
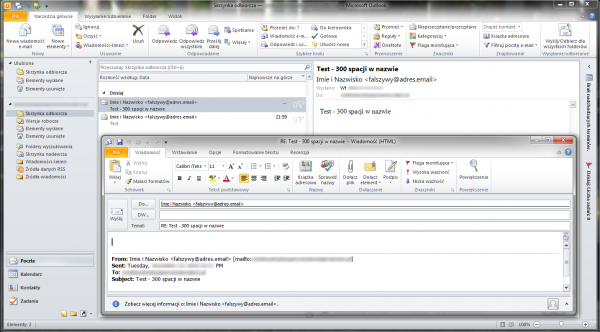
.LNK
LNK files have recently regained popularity during the campaign with „ransomware” malware (e.g. Locky). The attack consists in creating a shortcut to a given software along with additional commands that will run more advanced commands. Let’s take a look at how this technique works in order to know how to defend oneself against it.
PowerShell
PowerShell is willingly used in connection with the wide range of possibilities of abundance of a given command. With this method, the attacker probably takes the following steps:
- Creates a new shortcut together with the PowerShell command:
|
1 |
Command: %SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe -command "[System.Reflection.Assembly]::LoadWithPartialName(\"System.Windows.Forms\");[System.Windows.Forms.MessageBox]::Show(\"This is PowerShell - Simple Command\")" |
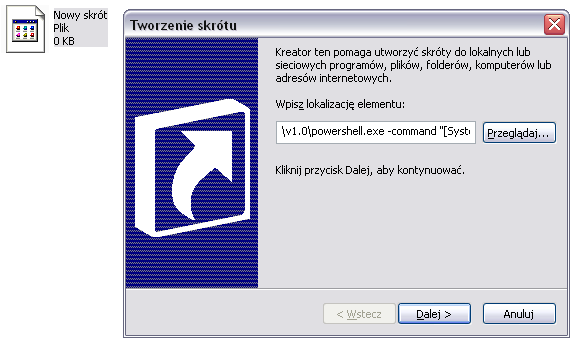
- Once created, the link looks like this:
- Then it changes its name and icon to another one, e.g.:
Our link is not “malicious” because it only contains a simple message. In normal use, an attacker may place there, for example, downloading another EXE file and running it.
It is worth mentioning that in the past we used to meet the link more often:
|
1 |
%SystemRoot%\System32\cmd.exe /c COMMAND_HERE |
If the attacker has already prepared a link, the next step is the way it is delivered:
- .LNK + Microsoft Office document
One of the options is a Word document:
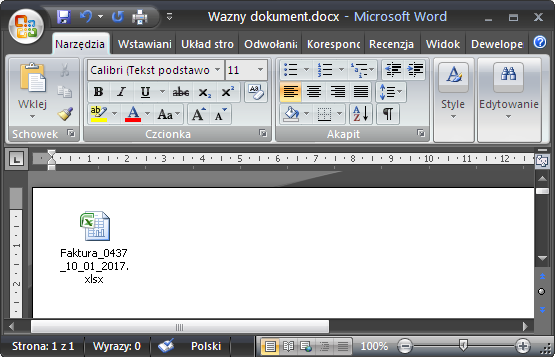
- .LNK + archive
Of course, a link prepared in this way (a .LNK file) can be placed in an archive, e.g. ZIP:
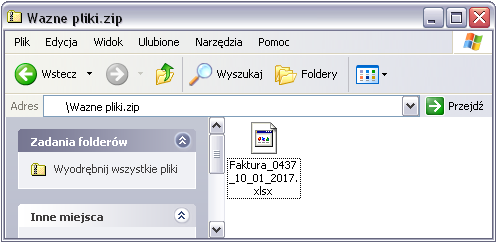
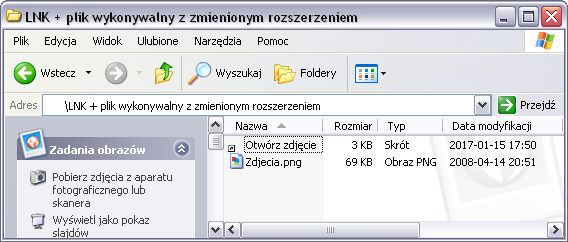
- .LNK + executable file with changed extension
Another technique is to change the executable file extension, e.g. EXE to PNG. Then the attacker only has to create a shortcut, with a command similar to the one below:
|
1 |
Command: %SystemRoot%\System32\cmd.exe /c Photos.png |
Summary
I hope the article will help readers to better recognize phishing. Of course, let’s not forget about sociotechnics, as well as malware, which is often attached to e-mails, among others. One has to keep in mind that the article does not exhaust the list of all attacks – only the “most interesting” ones are mentioned.
I recommend this article to all those who are interested in raising their awareness of possible attacks.